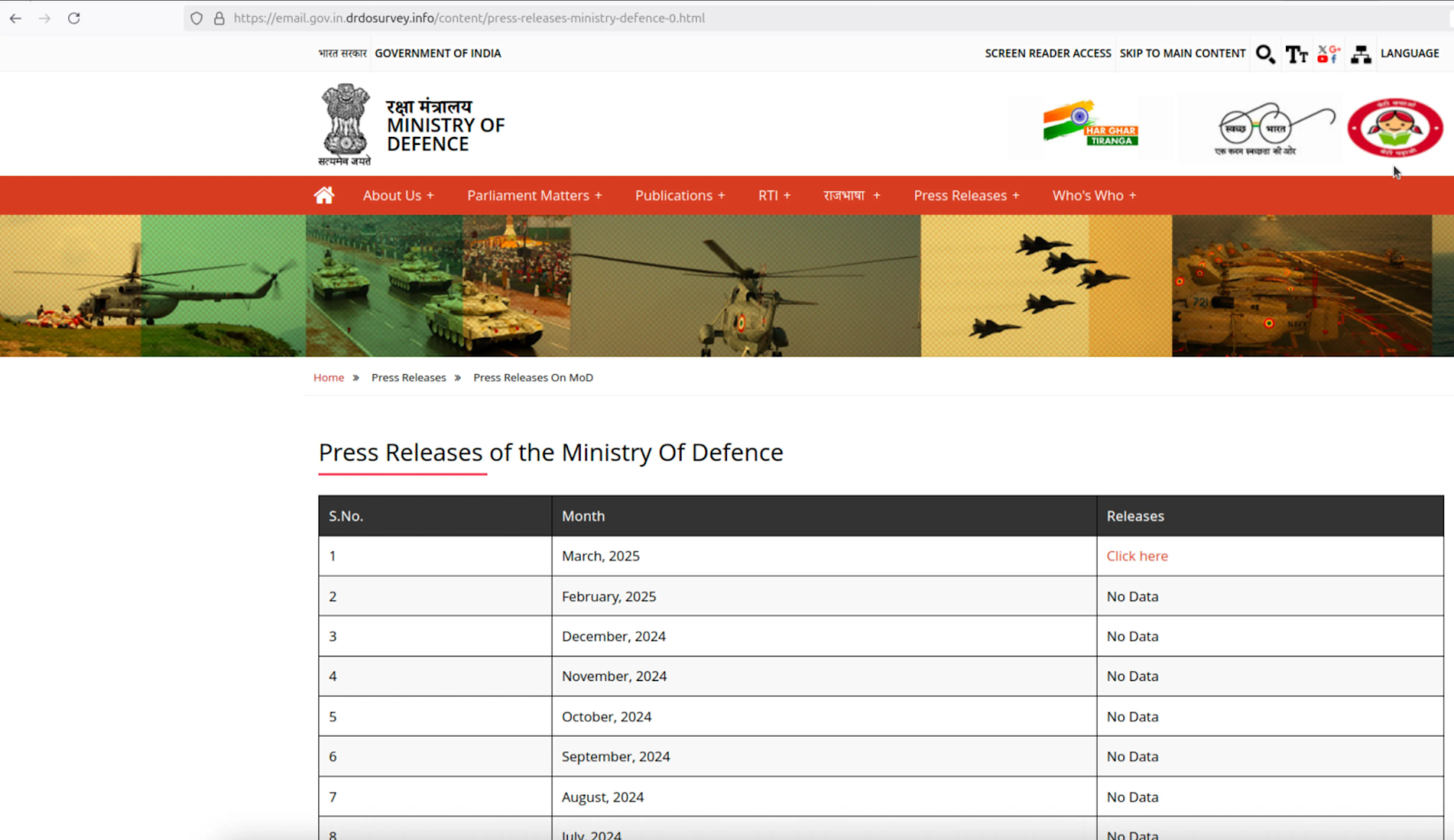
NEW DELHI: In the weeks leading up to and following the April 2025 Pahalgam massacre and the subsequent Operation Sindoor, a covert cyber campaign, traced to Pakistan, was quietly unfolding. With the intention to exploit the expected heightened public and institutional attention on official government updates, a Pakistan-aligned hacking group known as “APT36” launched a sophisticated phishing operation by cloning the Ministry of Defence’s press release portal.
As citizens, journalists, and officials increasingly visited the site for real-time information on security developments, the attackers used the fake page to deliver malware, gaining silent access to sensitive systems at a moment when India’s defence apparatus was most active—and most distracted. The campaign began around March 2025, when cybersecurity investigators discovered a website impersonating the official Ministry of Defence press release portal. Although the fake site closely resembled the real one, it contained only a single working link—marked as the “March 2025” release.
That link led users, depending on whether they were on Windows or Linux, into a trap. In the Windows version, clicking the link opened what looked like a government warning page labelled “For Official Use Only,” overlaid on a blurred image of a real ministry website. When users clicked “Continue,” a hidden script silently copied a command into their system clipboard. If the victim pasted and ran the command, it triggered a remote access attack, giving the hackers control of the machine.
The infection chain was designed to seem official and credible. The malicious command used a Windows program called mshta.exe to fetch a file from a spoofed domain resembling a legitimate Indian government address. This file ran a loader program called BroaderAspect, which quietly downloaded a decoy PDF to keep the user occupied while the real payload—a new version of a spying DRAT—was installed in the background. The loader also modified the Windows Registry to ensure that the malware would start automatically whenever the system was rebooted. The attackers didn’t stop with Windows.
The Linux version of the trap displayed a fake CAPTCHA page that asked users to click a button labelled “I’m not a rebot”—a deliberate misspelling. Behind the scenes, this button copied a command that, if pasted into a terminal, would download a shell script from the same attackercontrolled server. This cross-platform targeting reflected a broader intent: to maximize reach and ensure compatibility across India’s diverse digital infrastructure.
At the centre of this campaign was a modified version of DRAT—now dubbed DRAT V2—a powerful spying tool built to allow remote control of infected systems. This new variant, written in the Delphi programming language rather than the older .NET version, allowed the hackers to run arbitrary shell commands, collect sensitive files, maintain access, and even exfiltrate credentials. Although the malware did not employ advanced stealth techniques, its simplicity helped it avoid early detection.
The command-and control communication protocol was also updated to support both ASCII and Unicode input, offering flexibility during exploitation. The hacking group behind the operation was identified as TAG-140, which overlaps with SideCopy—a known subgroup of AP T36, also called Transparent Tribe. This collective has long been linked to Pakistan and is known for targeting Indian military, diplomatic, and government systems.
The group’s earlier operations had used various spying tools such as SparkRAT, AllaKore, Xeno RAT, and ReverseRAT. In this campaign, they added DRAT V2 to their arsenal, indicating a trend of rotating tools to evade detection and maintain access. Notably, the servers used in this attack were hosted by providers like Namecheap and HZ Hosting, located in the US and Netherlands, with domains such as trade4wealth[.]in and email.gov. in.drdosurvey[.]info used to spoof Indian government infrastructure. This cyberattack campaign came to light publicly in June 2025, when cybersecurity firm Recorded Future’s threat research division, “Insikt Group” released a detailed analysis, linking the infrastructure and malware to TAG-140 with moderate confidence.
The evidence included the use of previously seen malware loaders, overlaps in domain registration patterns, and targeting behaviour consistent with past APT36 operations. The strategic timing of the operation—coinciding with the April 2025 Pahalgam massacre and May’s Operation Sindoor—suggests a deliberate effort to exploit crisis periods when Indian government systems would be under pressure. Cybersecurity experts believe the goal was long-term infiltration and surveillance, with the fake ministry site acting as a baited gateway to plant espionage tools inside key networks.
Beyond DRAT V2, the broader pattern of attack revealed a widening of focus. In recent months, APT36 and affiliated actors have targeted India’s oil and gas sector, railways, foreign affairs, and even the healthcare and telecom industries. Virus and trojan elements were used in separate campaigns, often delivered via phishing emails disguised as official communication from Indian government bodies. Some attacks included PDF files with embedded executable code disguised by double extensions like .pdf. exe—designed to trick even experienced users.